KGpg: Difference between revisions
No edit summary |
add anchor for subpage linking |
||
| (15 intermediate revisions by 6 users not shown) | |||
| Line 1: | Line 1: | ||
<languages /> | <languages /> | ||
<translate> | <translate> | ||
<!--T:9--> | |||
__TOC__ | __TOC__ | ||
| Line 18: | Line 19: | ||
|} | |} | ||
== Extending the life of your keys == | == Extending the life of your keys == <!--T:10--> | ||
<!--T:11--> | |||
As you can see in the image above, you can extend the life of your keys using the <menuchoice>Change Expiration</menuchoice> button. Simply choose the new date from the popup calendar. To do this, however, you must have access to the private key and its pass-phrase. Without them you can do nothing. | As you can see in the image above, you can extend the life of your keys using the <menuchoice>Change Expiration</menuchoice> button. Simply choose the new date from the popup calendar. To do this, however, you must have access to the private key and its pass-phrase. Without them you can do nothing. | ||
= | </translate><span id="Change your passphrase"></span><translate> | ||
== Change your passphrase == <!--T:12--> | |||
<!--T:13--> | |||
Should you suspect your passphrase is compromised, you can change this also from the '''Key Properties''' dialogue. The <menuchoice>Change Passphrase</menuchoice> button is below <menuchoice>Change Expiration</menuchoice>. | |||
== Revoking a key == <!--T:14--> | |||
<!--T:15--> | |||
If you lose your private key or think it has been compromised in some way you need to revoke it. To reliably render a key unusable you need to revoke it. Revoking is done by adding a special revocation signature to the key. | If you lose your private key or think it has been compromised in some way you need to revoke it. To reliably render a key unusable you need to revoke it. Revoking is done by adding a special revocation signature to the key. | ||
<!--T:16--> | |||
The revocation signature can be created together with the key. In this | The revocation signature can be created together with the key. In this | ||
case it is stored in a separate file. This file can later be imported into | case it is stored in a separate file. This file can later be imported into | ||
the keyring and is then attached to the key rendering it unusable. | the keyring and is then attached to the key rendering it unusable. | ||
<!--T:19--> | |||
{{Warning|1=Please note that to import this signature to the key no password is required. Therefore you should store this revokation signature in a safe place, usually one that is different from you key pair. It is a good advise to use a place that is detached from your computer, either copy it to an external storage device like an USB stick or print it out.}} | |||
<!--T:17--> | |||
If you have not created such a detached revocation on key creation you can | If you have not created such a detached revocation on key creation you can | ||
create such a revocation signature at any time choosing <menuchoice>Your Key -> Revoke key</menuchoice>, optionally importing it to your keyring immediately. | create such a revocation signature at any time choosing <menuchoice>Your Key -> Revoke key</menuchoice>, optionally importing it to your keyring immediately. | ||
{{Note|1= | <!--T:18--> | ||
{{Note|1=The option to revoke a key has only been available in the context menu until KDE SC 4.7.1. Since then it has been moved to the key menu. }} | |||
<!--T:4--> | <!--T:4--> | ||
{{Tip|When you start '''KGpg''' with default settings it will hide in the system tray. If you started '''KGpg''' and do not see it anywhere you can probably reach it when you expand the [[Special:myLanguage/Plasma|Plasma]] system tray widget.}} | |||
<!--T:8--> | <!--T:8--> | ||
{{Tip|1=If a contact has more than one key - perhaps some old keys in addition to the current one - and the wrong key is being used for encryption, find the old keys and reduced their Trust status to Not Trusted. They will remain available for decrypting old messages, but not used for new ones. }} | |||
<!--T:5--> | <!--T:5--> | ||
[http://docs.kde.org/development/en/kdeutils/kgpg/index.html A full illustrated manual] helps you through | [http://docs.kde.org/development/en/kdeutils/kgpg/index.html A full illustrated manual] helps you through some details. | ||
<!--T:6--> | <!--T:6--> | ||
If you are not in a position to physically verify the identity of your contacts you should especially read [http://docs.kde.org/development/en/kdeutils/kgpg/manage.html#keysigning the key-signing section] which explains the benefits of local-signing. | If you are not in a position to physically verify the identity of your contacts you should especially read [http://docs.kde.org/development/en/kdeutils/kgpg/manage.html#keysigning the key-signing section] which explains the benefits of local-signing. | ||
== Tutorials == <!--T:23--> | |||
<!--T:24--> | |||
* [https://peertube.mastodon.host/videos/watch/bc82c21b-7526-44be-8efb-ede6edac51af Verify GPG signatures with KGpg inside Dolphin] (Source Peertube instance: peertube.mastodon.host) | |||
== More Information == <!--T:20--> | |||
<!--T:21--> | |||
* [[Special:myLanguage/Concepts/OpenPGP_For_Beginners|Explanation of OpenPGP concepts for beginners]] | |||
<!--T:22--> | |||
* [https://www.gnupg.org/documentation/howtos.en.html The base software: GnuPG] | |||
<!--T:25--> | |||
* [https://docs.kde.org/stable5/en/kdeutils/kgpg/index.html '''KGpg''' manual] | |||
<!--T:7--> | <!--T:7--> | ||
[[Category:Utilities]] | [[Category:Utilities]] | ||
[[Category:Security]] | [[Category:Security]] | ||
[[Category:Privacy]] | |||
</translate> | </translate> | ||
Latest revision as of 06:12, 27 October 2022
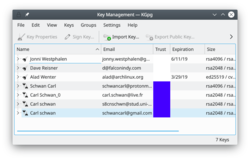 |
KGpg provides a graphical interface to gpg's commands |
GnuPG encrypts and decrypts your mail and selected files. There are many command-line options to achieve this. With KGpg the anxiety is removed - you don't have to remember any commands. KGpg can help you set up and manage your keys, import and export keys, view key signatures, trust status and expiry dates. In fact just about everything you need to do is covered by KGpg. A wizard is provided to help you set up your keys.
KGpg is integrated into Konqueror and Dolphin, where a context menu allows you to choose to encrypt a file, with or without signing.
 |
 |
Extending the life of your keys
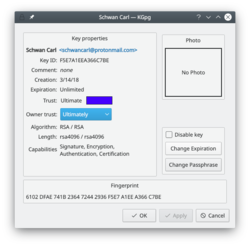
As you can see in the image above, you can extend the life of your keys using the button. Simply choose the new date from the popup calendar. To do this, however, you must have access to the private key and its pass-phrase. Without them you can do nothing.
Change your passphrase
Should you suspect your passphrase is compromised, you can change this also from the Key Properties dialogue. The button is below .
Revoking a key
If you lose your private key or think it has been compromised in some way you need to revoke it. To reliably render a key unusable you need to revoke it. Revoking is done by adding a special revocation signature to the key.
The revocation signature can be created together with the key. In this case it is stored in a separate file. This file can later be imported into the keyring and is then attached to the key rendering it unusable.
If you have not created such a detached revocation on key creation you can
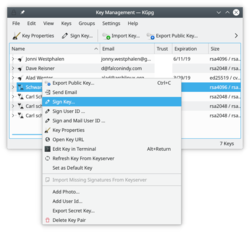
create such a revocation signature at any time choosing , optionally importing it to your keyring immediately.
A full illustrated manual helps you through some details.
If you are not in a position to physically verify the identity of your contacts you should especially read the key-signing section which explains the benefits of local-signing.
Tutorials
- Verify GPG signatures with KGpg inside Dolphin (Source Peertube instance: peertube.mastodon.host)



