KGpg/fr: Difference between revisions
(Created page with "== Étendre le vie de vos clés ==") |
|||
| Line 14: | Line 14: | ||
|} | |} | ||
== | == Étendre le vie de vos clés == | ||
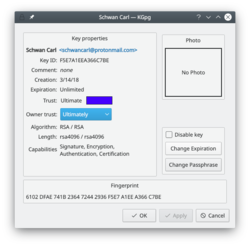
As you can see in the image above, you can extend the life of your keys using the <menuchoice>Change Expiration</menuchoice> button. Simply choose the new date from the popup calendar. To do this, however, you must have access to the private key and its pass-phrase. Without them you can do nothing. | As you can see in the image above, you can extend the life of your keys using the <menuchoice>Change Expiration</menuchoice> button. Simply choose the new date from the popup calendar. To do this, however, you must have access to the private key and its pass-phrase. Without them you can do nothing. | ||
Revision as of 14:20, 16 November 2014
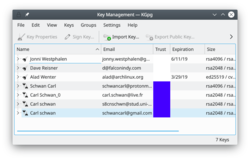 |
KGpg fournit une interface graphique aux commandes de gpg |
GnuPG chiffre et déchiffre vos e-mails et les fichiers que vous avez choisi. Il y a plusieurs options de ligne de commande pour réaliser cela. Avec KGpg, l'anxiété disparait - vous n'avez pas besoin de vous rappelez les commandes. KGpg peut vous aider à paramétrer et à gérer vos clés, à importer et exporter des clés, à voir les signatures des clés, le statut de confiance et les dates d'expiration. En fait, tout ce dont vous avez besoin est pris en charge par KGpg. Un assistant est présent pour vous aider à paramétrer vos clés.
KGpg est intégré dans Konqueror et Dolphin, où un menu contextuel vous permet de choisir de chiffrer un fichier, avec ou sans signature.
 |
 |
Étendre le vie de vos clés
As you can see in the image above, you can extend the life of your keys using the button. Simply choose the new date from the popup calendar. To do this, however, you must have access to the private key and its pass-phrase. Without them you can do nothing.
Change your passphrase
Should you suspect your passphrase is compromised, you can change this also from the Key Properties dialogue. The button is below .
Revoking a key
If you lose your private key or think it has been compromised in some way you need to revoke it. To reliably render a key unusable you need to revoke it. Revoking is done by adding a special revocation signature to the key.
The revocation signature can be created together with the key. In this case it is stored in a separate file. This file can later be imported into the keyring and is then attached to the key rendering it unusable.

If you have not created such a detached revocation on key creation you can
create such a revocation signature at any time choosing , optionally importing it to your keyring immediately.


A full illustrated manual helps you through every detail.
If you are not in a position to physically verify the identity of your contacts you should especially read the key-signing section which explains the benefits of local-signing.
