KGpg/zh-tw: Difference between revisions
(Updating to match new version of source page) |
(Updating to match new version of source page) |
||
| Line 44: | Line 44: | ||
If you are not in a position to physically verify the identity of your contacts you should especially read [http://docs.kde.org/development/en/kdeutils/kgpg/manage.html#keysigning the key-signing section] which explains the benefits of local-signing. | If you are not in a position to physically verify the identity of your contacts you should especially read [http://docs.kde.org/development/en/kdeutils/kgpg/manage.html#keysigning the key-signing section] which explains the benefits of local-signing. | ||
== Tutorials == | |||
* [https://peertube.mastodon.host/videos/watch/bc82c21b-7526-44be-8efb-ede6edac51af Verify GPG signatures with KGpg inside Dolphin] (Source Peertube instance: peertube.mastodon.host) | |||
== More Information == | == More Information == | ||
| Line 51: | Line 55: | ||
* [http://www.gnupg.org/documentation/howtos.en.html the base software: GnuPG] | * [http://www.gnupg.org/documentation/howtos.en.html the base software: GnuPG] | ||
[[Category: | [[Category:Utilities]] | ||
[[Category: | [[Category:Security]] | ||
[[Category:Privacy]] | |||
Revision as of 14:30, 13 May 2019
 |
KGpg為gpg命令提供了圖形介面 |
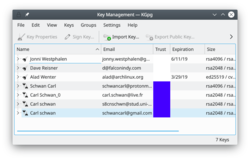
GnuPG加密和解密你的郵件和選定的文件。完成這樣的操作需要很多的命令選項。有了KGpg憂慮就可以消除了-你不再需要記住任何命令。 KGpg幫你建立和管理你密鑰,導入和導出密鑰,查看密鑰簽名,信任等級和有效期。實際上差不多所有你需要做的事情 KGpg都覆蓋到了。同時也提供嚮導幫助你建立你的密鑰。
KGpg is integrated into Konqueror and Dolphin, where a context menu allows you to choose to encrypt a file, with or without signing.
 |
 |
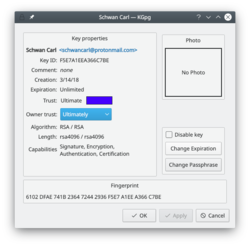
Extending the life of your keys
As you can see in the image above, you can extend the life of your keys using the button. Simply choose the new date from the popup calendar. To do this, however, you must have access to the private key and its pass-phrase. Without them you can do nothing.
Change your passphrase
Should you suspect your passphrase is compromised, you can change this also from the Key Properties dialogue. The button is below .
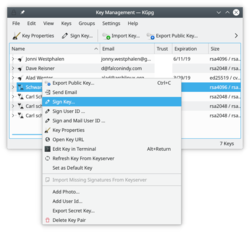
Revoking a key
If you lose your private key or think it has been compromised in some way you need to revoke it. To reliably render a key unusable you need to revoke it. Revoking is done by adding a special revocation signature to the key.
The revocation signature can be created together with the key. In this case it is stored in a separate file. This file can later be imported into the keyring and is then attached to the key rendering it unusable.

If you have not created such a detached revocation on key creation you can
create such a revocation signature at any time choosing , optionally importing it to your keyring immediately.


A full illustrated manual helps you through some details.
If you are not in a position to physically verify the identity of your contacts you should especially read the key-signing section which explains the benefits of local-signing.
Tutorials
- Verify GPG signatures with KGpg inside Dolphin (Source Peertube instance: peertube.mastodon.host)
